
Behind The Code: wpyii2 The Fake WordPress Plugin
Fake WordPress plugins abound. Learn the signs to keep yourself safe.
Introduction
In January, we wrote about the importance of knowing your code. In this month’s article, we will talk about a fake plugin that was discovered during an unrelated investigation on a customer site. We will highlight some of the techniques that can be used by site owners to help them determine whether a component is legitimate or not.
Discovery
The SiteLock Malware Research Team (SMRT) detected and remediated numerous phishing kits installed on a customer site in a variety of locations. These were targeting a variety of online resources ranging from the Saudi Post to DHL. During the remediation, we came across several WordPress installations with an unfamiliar plugin named ‘wpyii2’ that warranted additional investigation.
Investigation
PHP Header
The header comment of all WordPress plugins and themes contains information about the component, including the name, the location to download it from, a description, and the author information.
The header comment of our unfamiliar plugin file appears to be legitimate:

On the face of it, a WordPress plugin that integrates the Yii 2 framework could, potentially, make sense. So let us look at the details to see what we can find out.
Author URI
If we take the author URI, yiiframework [.] com, and search for it online, we find that it is, in fact, legitimate.

When we visit that site, we see the Yii Framework website that we would expect:

While this does not appear to be related the authors themselves, it is possible that they are contributors to the framework. So far, so good. This could still be a legitimate plugin.
The Author and Contributors
When we start searching for the author and contributors that are listed, we start to see some questionable results. First, we find a post on the WordPress forums that implies a plugin was “resurrected as malware” with the similar header information.


However, that is tempered by what appears to be a legitimate translation plugin for WordPress called rustolat that has the same authors:


As a result, it is a little hard to come to a firm decision about whether our wpyii2 plugin is legitimate or not. Let us check one more thing before we dive into the code.
The Plugin URI
Plugin URIs point users to the place they can download the plugin or get support. For free plugins, it usually points to WordPress.org. For premium plugins, the URI usually points to where you can purchase it. In the case of our wpyii2 plugin, the URI is claiming that we can find the plugin on WordPress’s own site:

However, when we visit that URI, WordPress tells us that the page could not be found!
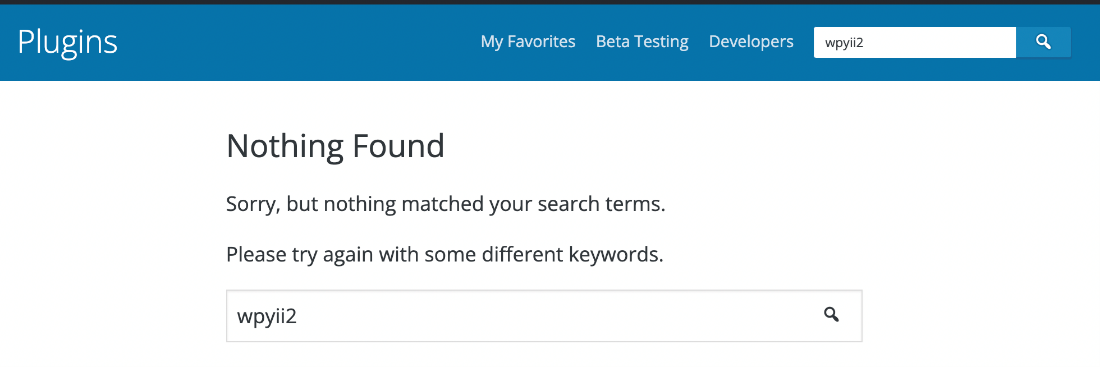
Something is not right with this ‘plugin’ that we have. Now we need to look at what it does.
Touring German Cities
A Curious Choice of Names
In the three variations SMRT found, the curious commonality was in the names of classes, variables, and functions, all of which were named for German cities.

That seems like an odd choice for a WordPress plugin and obfuscates their purpose in ways that are frowned upon by the style guides for WordPress and, in general, coding. It is hard to remember if München is a counter or a string or if Berlin is an authorization check, for example.
At this point, it is obvious that this is not related to the Yii Framework, let alone an actual WordPress plugin. But what do these fake plugins really do?
Decoding
The PHP code in these files is encoded in multiple ways and performs slightly different operations if it detects the presence of a DBHOST variable or an HTTP_HOST variable. Fortunately, neither of these are needed to fully decode the payload. We can comment out the evaluation statements (add_action and eval) and add echo statements to have the plugin print out the code instead of executing it.
WordPress Environments
If DBHOST is present, the plugin attempts to run add_action to hook into the WordPress install for persistence before calling a function and then evaluating a different value.

The code, when we print it out instead of evaluating it, makes references to a SMILODON package and performs some billing interaction with the SMILODON_URL:

The google-statik [.] pw URL is another component that attempts to perform a shell upload:


This is not something you want on your site.
Non-WordPress Environments
If DBHOST is not set, then the fake plugin decodes and runs a WSOX ENC shell.

This is, in every way, a typical webshell capable of uploading, modifying, and deleting files, executing PHP code, bruteforcing passwords on the server, modifying databases, and creating connections back to the attacker (backconnects), etc.


There it is. If it was not clear before, this makes it abundantly clear that this ‘wpyii2’ plugin is both fake and malicious.
Summary
Since discovery, SiteLock has removed this fake plugin from almost 200 sites in over 350 distinct install locations. It is always a good idea to review the components you have installed and remove plugins or themes that you are no longer using. However, be mindful as malicious plugins can or will hide themselves from the plugin list, so if you suspect that there are components present which you did not install, log in and check the files that are on your site.
If you suspect that your site has been infected with malware, SiteLock’s experts are here for you. Contact us today for assistance and let our team help you.
About The Author
Maarten Broekman has worked as a system administrator and systems engineer for over 25 years, primarily in the shared web-hosting space. One of the main concerns for web-hosting providers is being able to serve their customers’ websites as quickly and efficiently as possible. As a result, anything that detracts from performance needed to be examined closely and this is where his interest in malware and code analysis sprang from. For over a decade, finding, decoding, and removing malware (and automating that process) has been his primary focus.





