High Threat


|

Category: Shell / Information Disclosure
Trend Identified: 4/20/2017
CVE ID: N/A
Trend Name: Trend Tusayan
Vector: Application Vulnerability, Multiple
Complexity:
LOW: The vectors used to infect websites appear to be well-documented vulnerabilities in older versions of website platforms.
Confidentiality Impact:
HIGH: This infection provides complete control of the target website, including credential disclosure and database contents.
Integrity Impact:
HIGH: This infection provides the adversary administrator-level access to impacted website applications, making total data loss a possibility.
The SiteLock team has discovered a dangerous malware trend that not only provides website administrator level access to the bad actors involved, but exposes sensitive website credentials publicly over the internet.
The mechanism behind the trend involves the injection of the IndoXploit Shell, or IDX Shell, a common shell kit that is often used to deface and compromise websites. This particular trend makes extended use of the shell by grabbing the contents of configuration files for content management systems (CMS) including WordPress, Joomla and Magento, and saving them to .txt files in a folder it creates named /idx_config. While these text files may seem innocuous, they contain sensitive credentials that a hacker could use to access CMS-connected databases on target hosting accounts.

A Shell is a tool that can be used by an adversary to run commands in a hosting environment. Many hackers opt to upload a shell as the primary method for controlling a target environment.
We have identified that this trend currently impacts WordPress, Joomla and Magento websites by taking advantage of various vulnerabilities present in older versions of the platforms.
A website that has been infected will have a world-browsable folder called “idx_config,” which contains text versions of the configuration file of every CMS installation the shell is able to find.
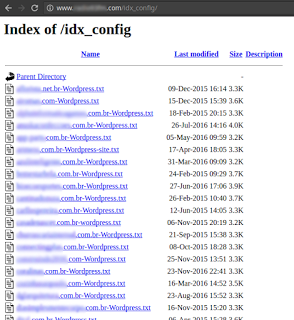
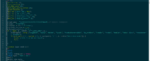
The code within the shell used to gain the initial foothold is currently listed in the SiteLock malware database, but does not appear to be widely recognized as a threat by many website security vendors at this time. You may use the code snippet below to manually add the shell to your security mechanisms.
As this trend both provides administrator-level control over the target website environment as well as publicly discloses credentials, action must be taken to counter both threats.
We advise reaching out to your hosting provider as they may have a backup of your website stored on file. Additionally, if you have any questions or concerns about how to protect your website, please contact us at 877.563.2832 or email [email protected].
Please check this article regularly for updates as more information becomes available.