
Malware Analysis Series — Part 1: Signature-Based Analysis
Back in February, a colleague and I delivered a talk on website security at WordCamp Miami. Among the many great questions we received both during the talk’s Q&A and at our sponsor booth, one common theme kept reoccurring from attendees: How does malware detection really work?
If you want to check out our WordCamp Miami talk, “Beyond the Basics: Building Security into Your Development Projects,” and the corresponding slides are available online.
Over the next few weeks, I’m going to explain different aspects of malware analysis, starting here…
There are a number of different methods that can be used in the detection of malware, including outside-in “black box” analysis of the public-facing website source code, which I recently wrote about, and inside-out “white box” analysis of web applications like WordPress. I’m going to talk a little more about some of the mechanisms behind white box malware analysis, namely signature-based code analysis and behavioral analysis. If you’re not familiar with white box analysis, get caught up by reading my article on white box analysis before continuing.
All caught up on white box and black box malware analysis? Good. Let’s talk shop.

Signature-Based Analysis
The old tried-and-true method utilized by security systems such as malware scanners and antivirus software abroad, signature-based analysis, scans the code contained within the target application looking for strings of code that match any known malware that’s already been cataloged within the malware database the scanner is using. Many mainstream malware scanners utilize signature-based analysis as a part of their scanning mechanisms. Signature-based analysis is flexible in that it can be used in both black box analysis (e.g. SiteLock® 360° Website Malware & Vulnerability Scanning) and white box analysis (e.g. SiteLock® SMART™ Scanning), basically wherever text-based analysis is possible. Signatures, also known as ‘definitions’ in some applications, are the individual iterations of code that have been documented by security researchers as malicious.
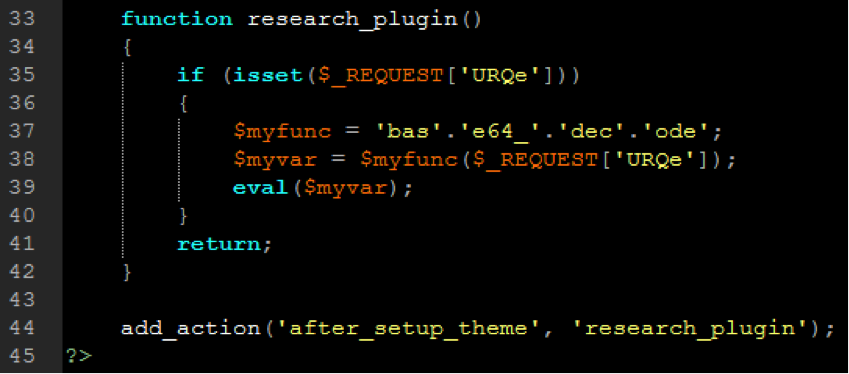
The speed of signature-based analysis makes it a popular go-to option for malware scanning; however, signature-based analysis is only capable of detecting malware that has already been documented, and relies on massive signature databases that have to be acquired from security firms and updated at very high frequency to remain effective. Unfortunately, signature-based analysis is also incapable of detecting zero day malware (malware that has not yet been documented), and is not terribly proficient at detecting new variations of old malware. Hackers have caught on that with signature-based analysis, they need only change around their code to evade detection. This is where behavioral analysis comes into the picture, which we’ll be discussing in Part Two of Ask a Security Professional’s Malware Analysis Series.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
Want to learn more about malware? Check out these additional resources from SiteLock:





