
How Hackers Consistently Gain Web Server Access
Overview
It is nothing new for hackers to try and keep consistent access on their victim web servers. There are a multitude of ways that this can be accomplished, however, there are two methods that we encounter the most:
- File upload bypasses.
- File downloads.
If an attacker finds these vulnerabilities, they can use them to continually upload their shells or download their backdoors in order to maintain access. As you can imagine, this can cause severe damage if gone unnoticed and not handled in a timely manner.
“Why does this matter?” Let’s say you are running an online business. When you advertise, search engines index your website so potential customers can see your products, reviews, updates, etc. without needing to visit your website. You may have noticed this when using your favorite search engine. For now, let’s say that your website gets hacked, and the attacker uses a script that will download spam files and edit the robots.txt file to allow search engines to index these spam files; and display those spam links instead of your normal links. This will effectively ruin your search engine ranking, drive away visitors, and potentially get your site backlisted for spam. To protect against these threats, it’s important to understand how these attacks are carried out.
Upload Bypass
One method attackers may use to upload their malware is by manipulating the file extension, such as changing .php to .PhP to avoid basic upload filters that only check that the file extensions are correct. However, a more complex method of avoiding filters is by abusing “magic bytes,” which is how Linux systems determine filetypes, unlike Windows systems which determine filetypes by the extension. Let’s look at an example SMRT found below.

The above file had the file name screenshot_1.png. As you can probably tell, there is PHP code in this image file. Using the file utility in Linux, we can see that this is not being registered as a PHP file or a PNG image file, as shown in the image below.
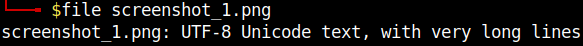
This will allow it to bypass filters that are not checking metadata and doing in-depth file checks. Now, whenever that file is loaded, the embedded PHP code will execute, downloading the malicious file.
The suspicious file can still be reached and was downloaded to a sandbox for further analysis. A snippet of the malicious code is shown below. Additionally, the SiteLock SMART Scanner already detects 0xmad[.]me should it be present in files on your website.
![Oxmad [.] Me](https://s3.us-east-1.amazonaws.com/sectigo-sites-web/sitelock/images/Oxmad-.-Me.png)
As stated in the code, this is a webshell used by the attacker to further exploit the website they have infiltrated. Notice the array of additional tools this webshell is able to download to keep access and modify settings.

To see exactly what the shell is doing, we ran the code in a sandbox environment.

As you can see from the image above, this webshell offers a full GUI for the attacker to make further exploitation easier. The webshell offers a wide range of functionalities, including uploading new files, running system commands and modifying existing files. This is a highly damaging malware infection as it can lead to repeat infections, persistent access for the attacker and even full site destruction. This shell will be cleaned by the SiteLock SMART scanner should it find it on the website it scans.
File Downloads
After an attacker figures out they can bypass upload restrictions, their next step is to download their own files to further exploit the website, whether it be for malicious redirects, SEO spam, or defacements.
One method an attacker may use to exploit systems is by using a simple PHP script to call out to their web server, save the code from a file, then run it on the target’s web server. A simple example of how this can be done was shown in the first image in the previous section.
Let’s look at another real-world example the SiteLock Malware Research Team (SMRT) discovered on a customer's website.

Right away, we can see suspicious activity going on. First, we see that there is a system call to the wget utility, which is used to download files or webpages over the internet. In this case, it is calling to the URL netbombers[.]site90[.]com/shell.zip. Once the download is complete, there is a dialogue box that will popup alerting the attacker to a successful download.
Next, the script will extract the malicious file to the directory that the ZIP file was downloaded too. Once that is done, the script will print out the directory listing using the ls command, presumedly to validate that the file was, in fact, successfully extracted.
To easily get to the malicious file, the attacker can include a GET request, that would look something like the example shown below.

If that GET parameter is included, the file will automatically redirect the attacker to the shell that was downloaded to the webserver using the built-in header PHP function.
While investigating the source of the malware, we found that the website hosting it was no longer in service at the time of writing, or at the very least, blocking our requests. This means that while this file is malicious, it will potentially not be able to accomplish its goal of downloading a shell.
We did notice that this malicious site seems to be currently migrating to a new server, so the issues connecting to the website could also be a temporary one for everyone trying to navigate to it.
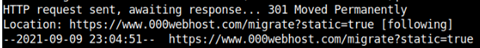
Trying to manually browse to the site also yields the same results, however it is a Cloudflare error 1020, meaning that the request to the website was blocked. This could also be temporary until the website finishes migrating before it starts distributing malware once more.
How The Vulnerabilities Get Introduced
As stated throughout the article, file upload vulnerabilities are introduced through improper validation of the uploaded file. The file download vulnerabilities can be introduced using unneeded functions being enabled on your website. There is also the threat of vulnerable plugins being installed or not being patched. A quick search on exploit-db for “wordpress file upload” revealed over 100 known file upload vulnerabilities in WordPress plugins. Some of the most recent ones are shown below.

Should you get a notification that there is an update for a plugin you are using, consult with your developer before updating the plugin to avoid any possible compatibility issues. It is recommended to update as soon as possible to mitigate the likelihood of the vulnerability being discovered on your website and exploited.
Summary
To prevent these kinds of vulnerabilities, make sure any file upload features that you use verify the files being uploaded match the filetypes that are expected.
For example, if you are allowing your visitors to upload images, the upload filter should check file extensions and the metadata for a definite answer as to whether the file is an image or an attempted malicious upload. This can be done with built-in PHP functions, such as exif_imagetype as this function will check the first bytes of the file and its signature to determine its image type. While it may be possible to still bypass that filter, it is possible to use additional filters for finding executable code in the file. This can be done using regular expressions to look for opening php tags or other strings that could alert to a malicious upload.
If malware bypasses those filters, some of the functions used, such as file_get_contents can be disabled in the php.ini file to prevent more files from being downloaded. It is recommended you speak with your web developer to ensure that those changes will not affect your website's functionality.
SiteLock’s website security solutions can help proactively prevent these types of attacks, even though these types of vulnerabilities can be difficult to track down and remediate. Our security solutions have the capabilities to find and remove malware that may be downloaded or uploaded because of these vulnerabilities. For example, both malware samples in this article will be cleaned by the SiteLock SMART scanner. However, if you feel your website is hacked or vulnerable, contact us to learn about our website security products or to speak with one of our security professionals about our services today.
About The Author
Adam Morris has worked in the information security field for the past four years, primarily in the web security space. Knowing information security is an ever-changing environment with new threats emerging every day, this evolving space is where his interest of finding new threats and exploits came from. For the past few years, researching new threats and new technologies has been his primary focus.





