
Fake Joomla! Plugin Keyscaptcha Still in the Wild
Fake plugins and extensions are a favorite, and particularly sneaky, way to inject malicious content into popular CMS platforms. Fake plugins disguise their malicious intent by mimicking the form and function of legitimate plugins. We will discuss a not-so-well-known fake Joomla! extension, what it does, and what you can do to protect your site from such attacks.
What We Found
The SiteLock Research team found several examples of a fake Joomla! extension named Keyscaptcha. Keyscaptcha mimics the legitimate Joomla! extension, KeyCAPTCHA for Joomla! 3.0. The first mention of this fake plugin was late 2015, and there are few if any mentions since.
The malicious file we found was /plugins/keyscaptcha/keysfunctions.php. Note that keysfunctions.php does not exist in the legitimate KeyCAPTCHA extension.
The keysfunctions.php file does not appear malicious at first glance. The code contains legitimate comments, contact information, and well documented functions.
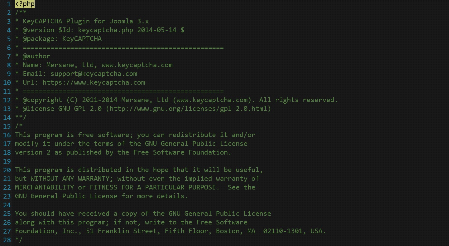
Keysfunctions code from fake Joomla! plugin
Scroll down a bit further and the malicious intent of the file becomes apparent.
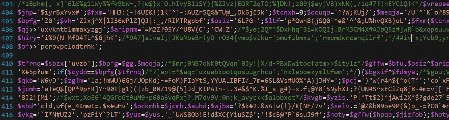
Keysfunction.php malware
The block of malware was filled with comments and other lines of code which appear to do nothing but attempt to confuse and obfuscate. Active code in the malware block consisted mainly of variable substitution and random strings that are then transformed into human readable output.
Simplified, the decoded malware was a password protected backdoor. It assigns content from encoded files to variables, base64 decodes the content, and executes the final result using PHP eval.
- Base64 is a content encoding method that takes content and transforms it into a defined set of 64 characters. It uses A-Z, a-z, 0-9, +, and /.
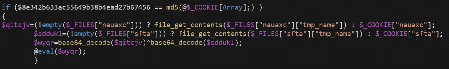
Decoded malware from fake plugin
The malicious Keyscaptcha plugin, which can provide bad actors with complete control of a site, has existed under the radar for over a year. If you find the Keyscaptcha malware on your site, the best course of action is to delete the entire /plugins/keyscaptcha directory. If you are utilizing the real KeyCAPTCHA plugin, it is a good idea to download a fresh copy of the plugin from the Joomla! Extensions Directory™.
It is also important to review all other site files, removing malicious content to mitigate further compromise. Using automated tools, like a malware scanning system in conjunction with a vulnerability scanner, can simplify this process.
The Malware is Gone, Now What?
First and foremost, keep plugins, extensions, themes, and the overarching CMS up to date by religiously backing up site data and applying updates. Most CMS platforms and their associated plugins and themes can be updated from their administrative dashboards in one or two clicks.
Next, regularly review all of your plugins, extensions, themes, and CMS installs. We recommend reviewing your files through FTP or hosting provider’s file manager periodically, as it is important to familiarize yourself with plugin names and file paths. This helps you become accustomed to what a normal directory structure looks like so anomalous files and directories, like fake plugins, stand out more easily.
If your website is the heart and soul of your business, we recommend investing in its security. SiteLock’s INFINITY scanning and malware removal service provides continuous scanning, automatic malware removal, and vulnerability remediation to significantly reduce the risk of attackers compromising your site, while SiteLock’s TrueShield web application firewall helps prevent infections before they begin.





