
Ask A Security Professional: DDoS Attacks — Part 4: Volumetric Attacks
So far in this #AskSecPro DDoS series we’ve covered both Application Layer DDoS Attacks and Protocol-Based DDoS Attacks. We’ve also identified the differences between a DoS and a DDoS attack. In this final segment of the DDoS series, we’ll discuss the third category of DDoS attacks, Volumetric Attacks, also known as Volume-Based Attacks
Volumetric DDoS Attacks
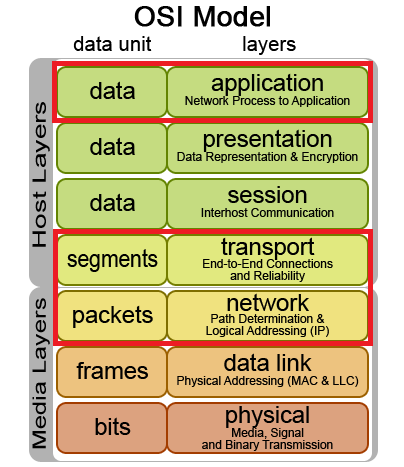
In the world of DDoS attacks, volumetric attacks aren’t just the 800-pound gorilla — they’re Kong; the towering behemoth that scales skyscrapers and swats aircraft from the sky. Volumetric attacks include some the largest attacks ever recorded by volume (pun intentional) by often exceeding 100Gbps in bandwidth. DDoS attacks in the Volumetric category span layers 3, 4, and 7 of the OSI model, accounting for about 65 percent of all DDoS attacks in the wild.

Volume-Based Attacks are measured in magnitude by bits per second (Bps).
Volumetric attacks are inherently simple attacks that require very little initial resources to generate a massive punch. Volumetric attacks introduce the concept of distributed reflected denial-of-service attack (DRDoS), which get their teeth through the use of a reflection medium. This is usually done by utilizing innocent third-party servers to perform the actual bombardment against the target server. By using a reflection medium, the adversary can amplify the outgoing attack at factors much higher than you might expect. In fact, there are many legitimate protocols that can be abused to accomplish massive gains in amplification. In some cases, the amplification factor can reach into the hundreds!
| • DNS (x28-54) | • SSDP (x30.8) | • Quake Network Protocol (x63.9) |
| • NTP (x556.9) | • CharGEN (x358.8) | • Steam Protocol (x5.5) |
| • SNMPv2 (x6.3) | • QOTD (x140.3) | • Kad (x16.3) |
| • NetBIOS (x3.8) | • BitTorrent (x3.8) |
One of the heavier-hitting attacks is called an Amplified NTP DDoS. Amplified NTP DDoS attacks rely on the exploitation of the Network Time Protocol’s (NTP) monlist feature, which is enabled by default on many servers in the wild. Sending a monlist command prompts the third-party server to list the last 600 IP addresses connected to the NTP server. To weaponize this feature, the adversary spoofs the target server’s IP address so that when the NTP server sends the response, it is sent to the target server instead. Because the size of the response is disproportionately larger when compared to the short command sent, an amplification factor of 556.9 is achieved.
The same logic of amplification can be applied to any of the protocols listed above. Meaning, the amount of data actually sent by adversary-controlled machines is very small, but the response from third-party servers is quite large. This brings to point the importance of not only protecting your server from DDoS attacks, but also protecting your server from playing a role in attacking someone else. By using a cloud-based web application firewall (WAF), like SiteLock TrueShield™, you’re able to mitigate both threats. Learn more about how SiteLock can help you defend against DDoS attacks.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!





