
Defacement Trend via REST API Exploit
|
SiteLock Research has identified a trend of defacements impacting thousands of WordPress websites. This trend of defacements appears to be exploiting a vulnerability in the WordPress REST API present in versions 4.7 and 4.7.1. The attack overwrites existing WordPress posts with a defacement, of which there are already many variations, with hackers even overwriting each others’ defacements in many cases. Customers using the SiteLock TrueShield™ Web Application Firewall (WAF) are protected against this exploit.
Trend characteristics:
- This attack vector impacts WordPress sites running versions 4.7 and 4.7.1 with the REST API enabled.
- The attackers are sending the defacement payload over the REST API to modify and deface existing posts.
- Post keywords are being modified in many cases, possibly for blackhat SEO purposes.
- We’ve identified at least six different defacement
campaigns through this vector.
Examples (hackers’ handles redacted):
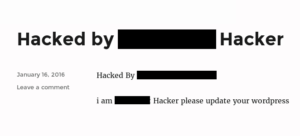
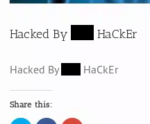

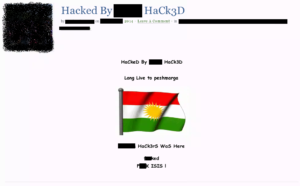
This attack targets existing posts in WordPress, which means that a successful attack is overwriting data inside the WordPress database and data may only be recoverable via backup. If you have been impacted by this attack, your best course of action is to follow these steps:
1. Perform a file and database backup of the impacted website and save it to a secure location. This will ensure your data is safe if any critical failures occur in the following steps.
2. Update WordPress to the latest version, version 4.7.2.
3. Login to /wp-admin/ and verify which posts have been impacted by the defacement by looking in the title and body of the post for content that you did not put there. From the “edit post” menu, for each impacted post, check the revision history of the post to see if the original content is intact in a previous revision. If a previous revision is available, restore the post to that revision. Be sure to also check if the permalink for the post has been modified.
In many cases, following the above steps will remove the defacement and no further action is required. If you were not able to recover all of your post content, please continue with the following steps.
4. Locate your most recent database backup from before the attack and restore it to the production database.
5. Login to /wp-admin/ to check if any database clean-up is required to synchronize to the current WordPress version on the production site.
6. If WordPress indicates database changes are needed, allow it to run through the changes.
7. Audit your website for any incompatibility with the new WordPress version you’ve installed. Issues with updating are most commonly evident in the look and feel of the website.
We advise reaching out to your hosting provider as they may have a backup of your website stored on file. Additionally, if you have any questions or concerns about this email, please contact us at 877.563.2832 or email [email protected].
Please check this article regularly for updates as more information becomes available.





