
Ask A Security Pro: DDoS Attacks — Part 2: Application Layer Attacks
In our last #AskSecPro article we discussed the differences between a DoS and a DDoS attack. Now that we understand what a DDoS attack is in concept, let’s learn a little more about the mechanisms involved in these attacks. In Part Two of the DDoS Attacks series we’ll focus on some of the attack vectors utilized by adversaries when launching a denial of service attack.
Generally speaking, DDoS attack vectors can be roughly classified into three categories, Application Layer Attacks, Protocol-Based Attacks, and Volumetric Attacks. When preparing to launch a targeted attack, the experienced adversary will take into account the defensive measures the target has, the software being used by the target, and the resources available to the adversary to execute the attack, such as botnet capacity. Taking this information into account helps the adversary decide which vector will have the most impact on the target. In more generic attacks where the adversary’s agenda may be little more than to gain attention, you may see this logic worked backward, first taking into account their resources before selecting a soft target susceptible to the attack. Here at SiteLock, we see more than our fair share of each classification hit SiteLock TrueShield™ throughout any given week. Today we’ll talk about Application Layer Attacks.
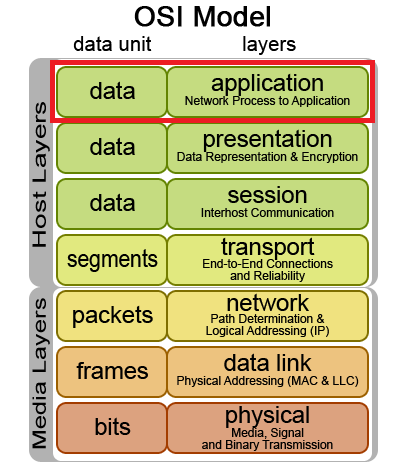
Application Layer DDoS Attacks
Application Layer Attacks, also known as Layer 7 Attacks after the OSI model, include attacks that target vulnerabilities in a server’s web services like Apache, IIS, NGINX, and so on, as well as floods using GET and POST methods over HTTP/S. This DDoS vector accounts for about 20 percent of all DDoS attacks. One recent example of Application Layer Attacks were the Mirai attacks on Dyn’s DNS servers that recently caused massive internet outages, where a botnet was formed using devices from the internet of things to leverage the attack.

Application Layer Attacks are measured in magnitude by requests per second (rps).
Specifically in the world of WordPress, the most notable recent example of an Application Layer Attack would be the xmlrpc.php DDoS attacks that initiated POST floods in the form of pingbacks, where the adversary would provoke a third-party server to send a pingback to a victim server in a sort of reflective attack using functions in WordPress’ xmlrpc.php file. The exploit was used broadly and extensively, succeeding in causing numerous temporary service outages for WordPress websites across the world. The simplicity of executing an xmlrpc.php-based attack precipitated its widespread use, which could be accomplished through a very small amount of code, like that seen below.
<methodCall> <methodName>pingback.ping</methodName> <params> <param><value><string><strong>http://victim</strong></string></value></param> <param><value><string><strong>http://reflector</strong></string></value></param> </params> </methodCall>
However, not all Application Layer Attacks can be executed with such ease. Experienced adversaries often put an extraordinary amount of planning into an attack that involves a significant amount of code and complexity. For example, by deploying droves of custom-built headless PhantomJS browsers installed on the computers of botnet zombies, and capable of storing session cookies, as well as mimicking the fingerprints of a regular visitor’s browser. SiteLock’s TrueShield™ Web Application Firewall network witnessed such an advanced persistent attack, dubbed a headless-browser DDoS, from a 180,000-zombie compound botnet which peaked at over 6,000 hits per second and lasted for over 150 hours.
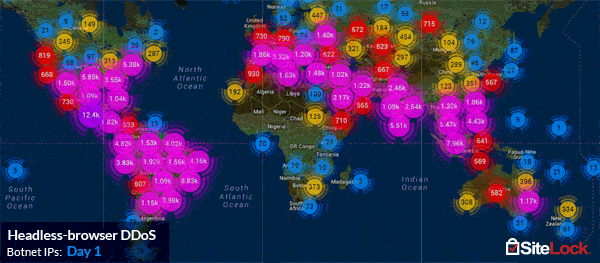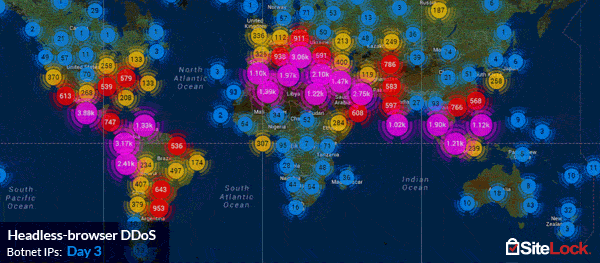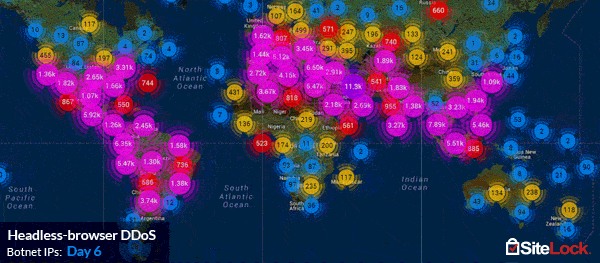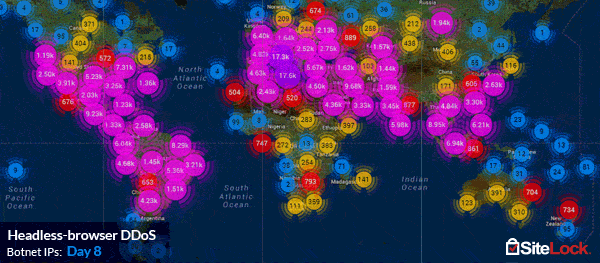
The varying complexity of Application Layer Attacks has established that no one mitigation method is capable of defending against them all, which is where many endpoint solutions may fall short. The most effective way of defending against the massive variance of vectors is through use a distributed cloud-based web application firewall, such as TrueShield™, which protects against DDoS attacks across layers 3, 4, and 7. Learn more about how SiteLock can help you defend against DDoS attacks.
In our next episode of Ask a Security Professional, we’ll be talking about Protocol-Based DDoS Attacks. Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!





